This article is the first of a series of articles providing an overview of security challenges in cloud computing, and respective solutions addressing such challenges.
By enabling a long-held dream of computing as utility (1), Cloud Computing has become one of the major technology trends in the last decade. Due to its’ flexible and agile nature, Cloud Computing is continuously and significantly transforming a large part of the IT industry (2). Its’ philosophy shift from a system- to a service-oriented approach has paved the way to develop innovative ideas, i.e. new services and/or business models, without the necessity of large capital expenses in computing and/or human resources. In addition, Cloud Computing naturally supports the raise of so called data economy, i.e. the ability to monetize data, for instance through big data analytics (3,4), or by enabling new paradigms such as “bring users to the data”, especially relevant in fields processing very large amounts of data, like the space industry (5), or weather forecast institutions (6). However, despite the many benefits and use cases, one of the major concerns for adopting Cloud Computing is security (7).
Consequently, the main goal of this series of articles is to provide an overview of security challenges in Cloud Computing, and respective solutions addressing such challenges. In order to achieve this goal, this series introduces a two-way approach, a holistic and a pragmatic approach. The holistic approach focuses on security challenges in Cloud Computing from a big picture overview, introducing the necessary theoretical background and the respective, theoretical solutions. The pragmatic approach focuses on security challenges in Cloud Computing from a practical perspective, introducing implemented security controls and offered security products by various Cloud Service Providers. Further, identifying potential gaps of such controls and/or products. Last, but not least, providing best practices for addressing such gaps and securing the configuration and operation of various Cloud technology solutions. The first part of this series introduces the fundamentals of Cloud Computing.

Cloud Computing Fundamentals
In practice Cloud Computing is a synonym for “Somebody’s else’s, computer that can be accessed and used through the network, remotely”.
Even in this oversimplified model, depicted in Fig. 1, a number of security challenges arise:
- How to ensure that the client Alice uses is trustworthy?
- How to ensure that leaked information is session restricted, in case the client Alice uses is malicious?
- How to ensure that Alice is connected to the correct, remote computer?
- How to ensure that the remote computer Alice is connected to is trustworthy?
- How to ensure that leaked information is session restricted, in case the remote computer Alice is connected to is malicious?
- How to ensure that the remote computer is accessible only from specific networks and machines?
- How to ensure that the communication link is secured against eavesdropper?
- How to ensure that only authorized users have access to the remote computer?
- How to ensure that authorized users have access only to their data?
- How to ensure that Alice behaves secure while using Cloud services?
Note that for a thorough understanding and analysis of security in the context of Cloud Computing, it is necessary to introduce a standard baseline that is well-known, and largely accepted by the community. Such baseline regarding Cloud Computing is provided by the National Institute of Standards and Technology (NIST (8)), in the special publications 800-145, and 500-292.
Definition
Cloud Computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g. networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. NIST further defines Cloud Computing by describing five essential characteristics, three cloud service models, and four cloud deployment models. In addition, the Cloud Security Alliance describes three more characteristics of Cloud Computing. They are summarized in visual form and explained in detail below.
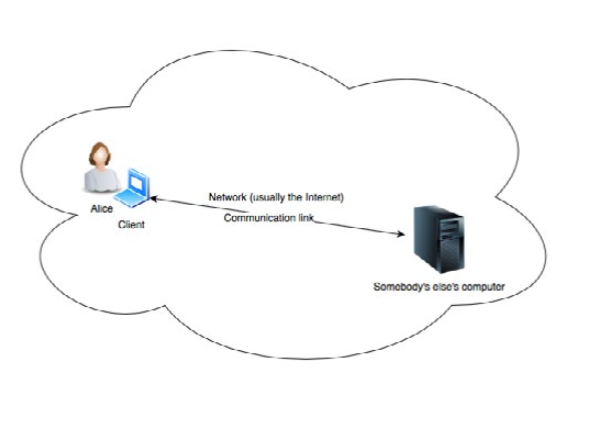
Fig 1: Simplified Model of Cloud Computing
Essential Characteristics
This section introduces eight essential characteristics of Cloud Computing. While the first five characteristics are introduced by the NIST special publication 800-145, the last three are introduced by Cloud Security Alliance.
On demand self-service
A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider.
Broad network access
Capabilities are available over the network and accessed through standard mechanisms that promote use of heterogenous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations.
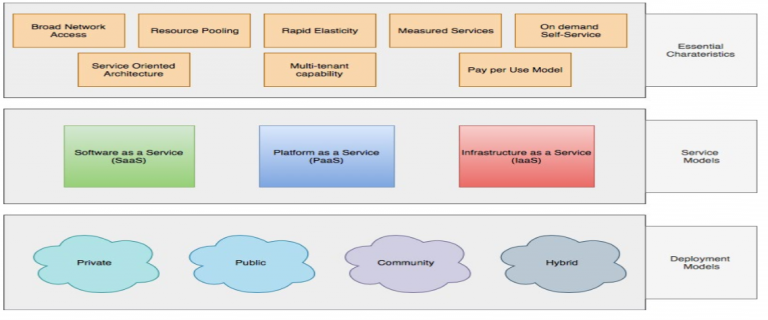
Fig 2: Characteristics, Service and Deployment Models in Cloud Computing
The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to customer demand. There is a sense of location independence in that the customer generally has no control or knowledge over the exact location of the provided resources but may be able to specify location at a higher level of abstraction (e.g., country, state, or datacenter). Example of resources include storage, processing, memory, and network bandwidth.
Rapid elasticity
Capabilities can be elastically provisioned and released, in some cases automatically, to scale rapidly outward and inward commensurate with demand. To the consumer, the capabilities available for provisioning often appear to be unlimited and can be appropriated in any quantity at any time.
Measured service
Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service (e.g. storage, processing, bandwidth, and active user accounts). Resource usage can be monitored, controlled, reported, providing transparency for both the provider and consumer of the utilized service.
Service Oriented Architecture
A basic requirement for Cloud Computing, as Cloud services are usually offered over REST-API.
Multi-tenant capability
A basic requirement for Cloud Computing, as resources are shared between different customers.
Pay per Use Model
Only the actually used resources are payed.
Service models
Software as a Service
The capability provided to the consumer is to use the provider’s application running on a cloud infrastructure. The applications are accessible from various client devices through either a thin client interface, such as a web browser (e.g. web-based E-Mail) or program interface. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage, or even individual applications capabilities, with the possible exception of limited user specific application configuration settings.
Platform as a Service
The capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created or acquired applications created using programming languages, libraries, services, and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure including networks, servers, operating systems, or storage, but has control over the deployed applications and possibly configuration settings for the application-hosting environment.
Infrastructure as a Service
The capability provided to the consumer is to provision processing, storage, networks, and other fundamental computing resources where the consumer is able to deploy and run
arbitrary software, which can include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, and deployed applications; and possibly limited control of select net- working components (e.g. host firewalls)
Deployment models
Private
The cloud infrastructure is provisioned for exclusive use by a single organization comprising multiple consumers (e.g. business units). It may be owned, managed, and operated by the organization, a third party, or some combination of them, and it may exist on or off premises.
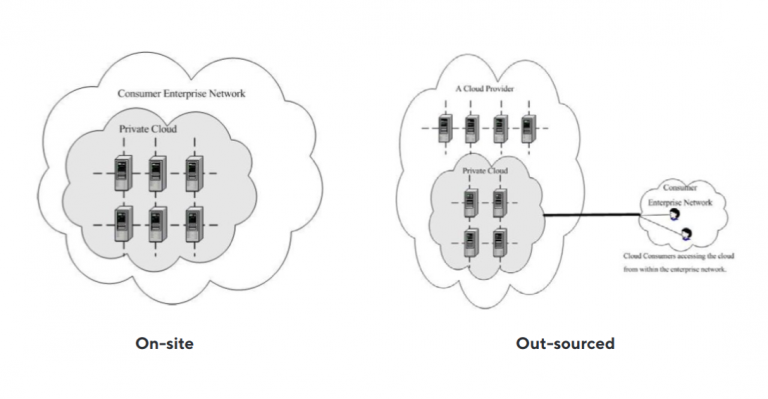
Fig 3: Deployment of a Private Cloud
Public
The cloud infrastructure is provisioned for open use by the general public. It may be owned, managed, and operated by a business, academic, or governmental organization, or some combination of them. It exists on the premises of the cloud provider.
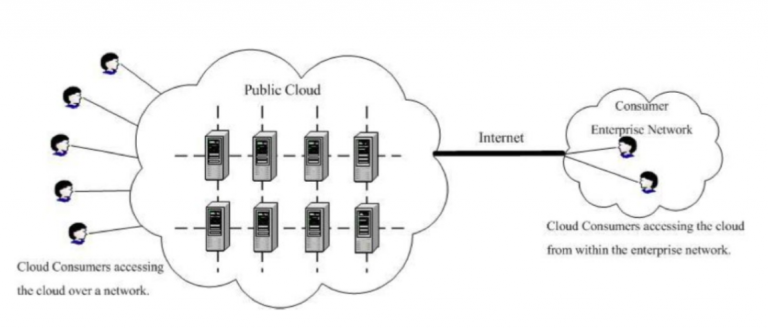
Fig 4: Deployment of a Private Cloud
Community
The cloud infrastructure is provisioned for exclusive use by a specific community of consumers from organizations that have shared concerns (e.g., mission, security requirements, policy and compliance considerations). It may be owned, managed, and operated by one or more organizations in the community, a third party, or some combination of them, and it may exist on or of premises.
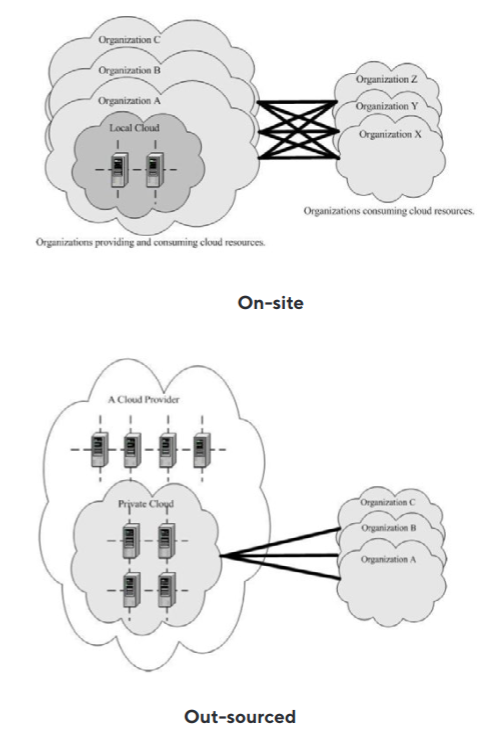
Fig 5: Deployment of a Community Cloud
Hybrid
The cloud infrastructure is a composition of two or more distinct cloud infrastructures (private, community, or public) that remain unique entities, but are bound together by standardized or proprietary technology that enables data and application portability (e.g. cloud bursting for load balancing between clouds).
Reference Architecture
The Cloud Computing reference architecture is introduced by NIST in the special publication 500-292. This reference architecture serves to identify the major actors, their activities and functions in Cloud Computing.
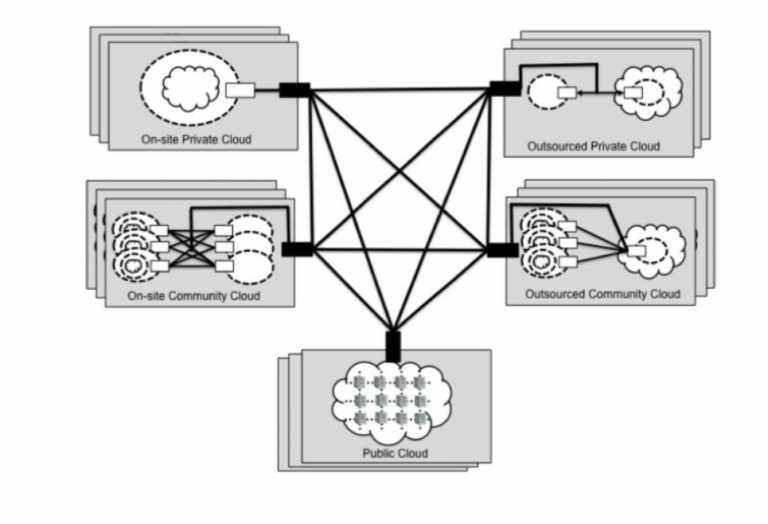
Fig 6: Deployment of a Hybrid Cloud
Cloud Consumer
A person or organization that maintains a business relationship with, and uses services from Cloud Providers.
Cloud Provider
A person, organization, or entity responsible for making a service available to interested parties.
Cloud Auditor
A party that can conduct independent assessment of cloud services, information operation systems, performance and security of the cloud implementation.
Cloud Broker
An entity that manages the use, performance and delivery of cloud services, and negotiates relationships between Cloud providers and Cloud consumers.
Cloud Carrier
An intermediary that provides connectivity and transport of cloud services form Cloud providers to Cloud consumers.
Scope Control
The management responsibility in Cloud Computing, depicted below, depends on the Cloud service type and whether the Cloud deployment is private. Thus, each Cloud Actor is responsible for implementing specific security controls throughout the life cycle of the Cloud environment.
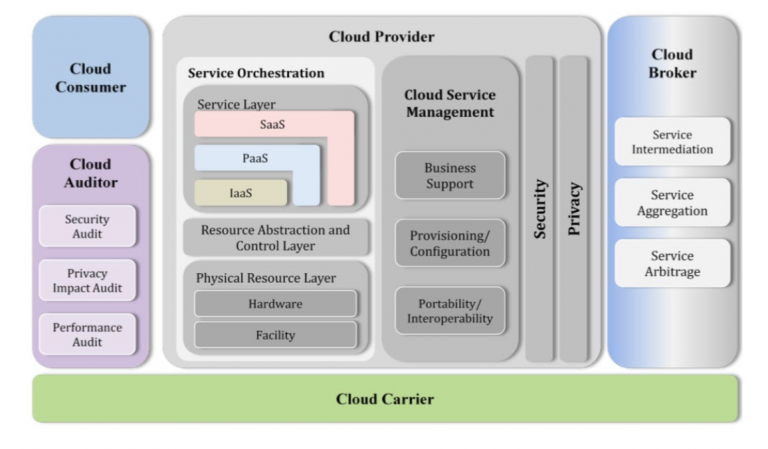
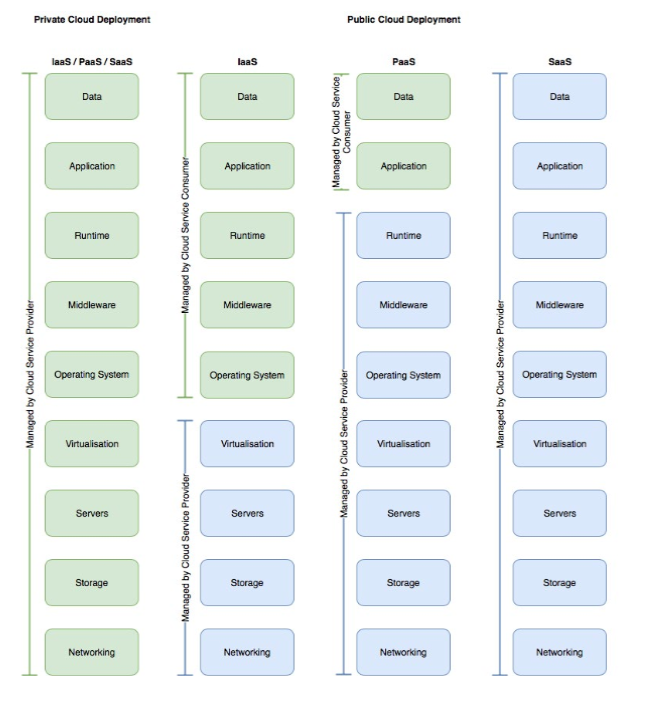
Fig 7: Scope Control in Cloud Computing
Sources:
-
- Parkhill, D. The Challenge of the Computer Utility. Addison-Wesley Educational Publishers Inc., US, 1966.
-
- Bayramusta, M., Nasir, V. A.. A fad or future of IT?: A comprehensive literature review on the cloud computing research. International Journal of Information Management, 2016, 36. Jg., Nr. 4, S. 635-644.
-
- Mosco, V.. To the cloud: Big data in a turbulent world.
Routledge, 2015
-
- https://bigdatawg.nist.gov/Day2_08_NIST_Big_Da- ta-Kearns.pdf, last accessed 27.08.2019
-
- https://eo4society.esa.int/wp-content/up- loads/2019/04/EO4Alps_Report_Roadmap.pdf, last accessed 27.08.2019
-
- https://indico.cern.ch/event/676472/ contributions/2905736/attachments/1609308/2555018/20180301_ECMWFs_IO_
and_Storage_Challenges_in_the_path_to_Exascale_Numerical_Weather_Prediction.v2.pdf, last accessed 27.08.2019
-
- Avram, M.. Advantages and challenges of adopting cloud computing from an enterprise perspective. Procedia Technology, 2014, 12. Jg., S. 529-534.
-
- https://www.nist.gov/

Dr. Jurlind Budurushi
Chief Cybersecurity Officer
jurlind.budurushi@cloudical.io
