Ten years after the zero trust security model was first articulated, organizations are doubling down – but successful defense also means reassessing your approach to operating the cloud.
A decade ago, Forrester Research analyst John Kindervag called time on perimeter security and warned us against trusting the traffic on our corporate networks. “With attackers becoming more sophisticated about insider threats, new security practices must be taken to stop them from spreading once inside networks,” Kindervag said.
The first decade of the 21st century marked a watershed in enterprise IT and security: the birth of cloud computing with AWS and Azure in 2006 and 2010, and the revolution in smart devices with Apple’s smartphone in 2007 and, three years later, its tablet. It was the dawning of digitalization – of applications, data and software moving off-premises to cloud operators with users accessing services via devices. Perimeter-based security, founded on firewalls and trusted IPs, was no longer sufficient to secure networks.
Ten years worth of experience plus the disruption of COVID-19 have helped to accelerate the pace of digitalization, while accentuating the risk posed to cybersecurity.
Remote working has become a permanent fixture as companies seek to operate in a COVID-19-safe way by rolling out more cloud to facilitate this. Digital has vaulted forward years in a matter of months, according to McKinsey, with one CIO calling events nothing less than “an historic deployment of remote work and digital access to services across every domain”.
With the increase in remote working, authentication from outside the office using VPN or RDP has surged, growing by 60 %. Criminals have, inevitably, attempted to exploit the situation, according to the FBI and Microsoft. Verizon’s 2020 Data Breach Investigations Report found the vast majority of criminals, 88 %, are in it for financial gain – to hold data, systems and organizations to ransom with the average cost of a breach hitting $ 3.8 m, according to IBM.
Many organizations have re-thought their cyber security in response. Ten years after Kindervag, Enterprise Management Associates reckons 60 % of IT buyers have accelerated the implementation of zero trust policies and technologies. It’s believed zero trust will help them prevent and contain breaches, mitigate unauthorized access and help improve their governance and compliance.
In the old world of perimeter security, once an intruder is on your network they can travel across systems unhindered. Under Kindervag’s approach, that’s not possible.
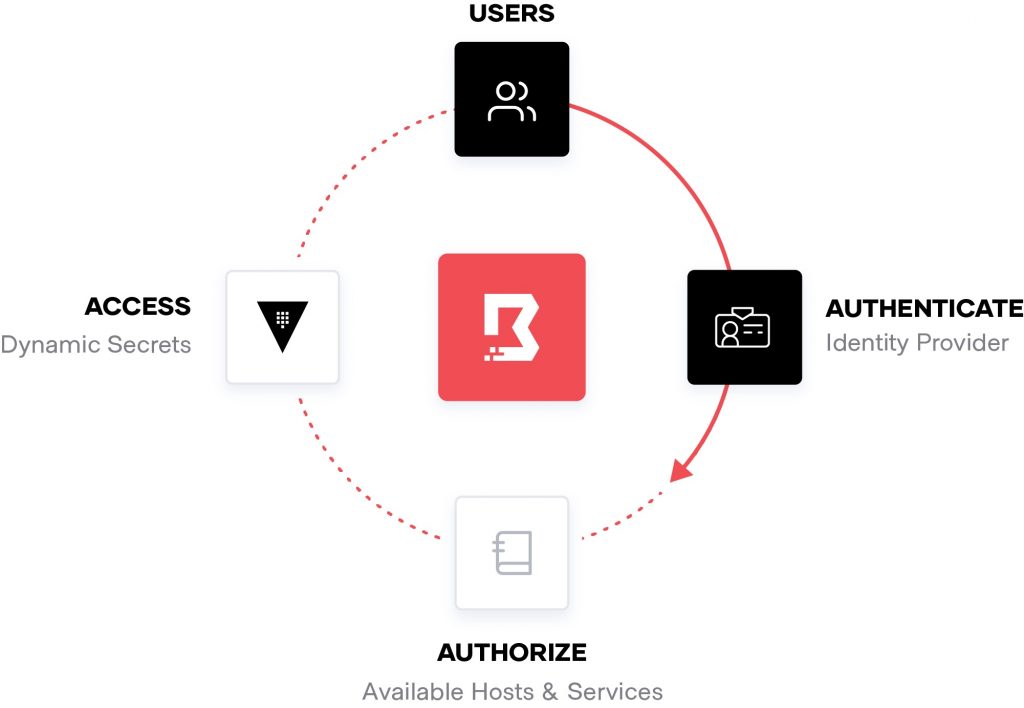
Fig. 1: Human-to-machine access
Sign me up. Wait…
Cloud, however, comes with two key features that present a considerable challenge to IT and security teams attempting to develop and enforce zero trust: scale and complexity.
Cloud is a form of highly-distributed computing that is far more complicated to develop and operate than traditional systems founded around a data center. Distributed computing has huge architectural and practical implications on compute, networking, security, availability, performance and resilience. Further complicating cloud is the notion of elasticity, allowing organizations to be more agile by being able to spin up and down instances with peaks in traffic. This involves a whole host of machine-to-machine, human-to-machine, and human-to-human transactions, communications and interactions (fig. 1 and fig. 2). These transactions can be fleeting – created for a single session or time window. Access to these systems and services is through endpoints – systems and networks that must be monitored and regulated through means of access and authorization that are both provisioned and reliably enforced. Such complexity and scale do not simply create more chinks in the perimeter through which data can be plucked – it creates a maze to manage.
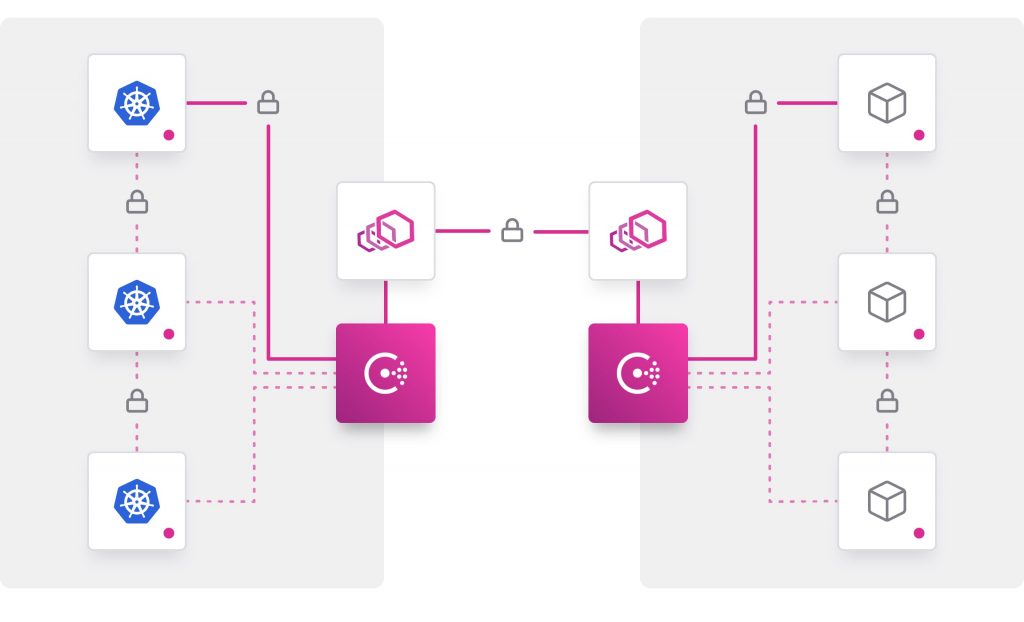
Fig. 2: Machine-to-machine access
Come in IP, your time is up
Overcoming this complexity and scale demands a different way of working. Forget being able to simply update existing data-center practices, tools and teams for the cloud.
Securing your network in a traditional data center configuration was a relatively simple, clearly defined task: you managed and secured a fixed, IP-defined perimeter through a combination of networks and firewalls, HSM, SIEMs and other physical access restrictions. This model, however, isn’t flexible or scalable enough for the dynamic and distributed nature of cloud.
The dynamic nature of connections and transactions in the cloud means IP addresses are ephemeral – they come and go as systems are spun up and down. The proliferation of machine-to-machine communications will mean not just a multitude of IP addresses but also that these addresses will be shared along with other system resources in the cloud. Oh, and your staff will log in to services using any number of devices with their own IP address from any location.
IP-based defense systems have two failings in the cloud: one it’s structurally complex to create and two, IP-based security systems are operationally difficult to implement and operate. They involve lots of overhead, take lots of experience and almost certainly have difficulty scaling. Moreover, IP addresses are no indicator of intent or trust: in a scenario where a user’s credentials might have been stolen or a device compromised, a trusted IP address could be a Trojan horse.
IP-based approaches were devised at a time when trust could be assumed. As Gartner’s Neil MacDonald explains: “IP addresses are weak identifiers at best and they can be spoofed.” An IP-based security model, even if it could be made to scale, would therefore be built on weak foundations.
Take a number, and get in line
Another on-prem approach that you see transposed to the cloud involves use of ITIL. With ITIL, the classic challenge is organization and process. Individuals and teams will typically have been arranged around a series of technology silos: if you raise a problem or need something fixed in this model then you file a ticket against that technology team and you wait for a response.
This has two problems: First, the time it can take to tackle a security issue can mean the difference between stopping an intruder and having to shell out a king’s ransom for the return of your data or to regain control of your systems. According to an IBM and Ponemon report from 2018, it takes an average of 197 days to identify a breach and 69 days to contain a breach; those who contain a breach in less than 30 days saved on average more than $ 1 m versus those who take longer.
The second problem for ITIL-based systems is operational: to be effective, a cloud security system must be capable of capturing the state of systems in the moment, of monitoring and managing them and of letting staff respond in real time. The complex and ephemeral state of machine-to-machine and people-to-machine transactions and communications in the cloud will challenge the ability of any ticket-based system to record and respond to incidents efficiently.
Time to operationalize
IP and ITIL are manifestations of a bigger issue when building zero trust in the cloud – a belief that the cloud can be run through a series of unintegrated, specialist tools and procedures.
EMA found that, in the debate over zero trust, tools were the focus for many organizations. For around a third surveyed, the main roadblocks to building zero trust are a lack of skills, tools and processes. More worrying is the fact that there is considerable disagreement in around a quarter of organizations about the technologies to use and who should operate or administer them.
Clearly, there’s a trap in the making here: it’s wrong to search for that zero trust silver bullet – a tool or product that will help secure your cloud in the post-perimeter jungle.
As Kieran Norton, infrastructure solution leader of Deloitte points out, it’s important to develop an operational appreciation of your cloud – not simply buy more product. “At the end of the day, it [zero trust] is an approach and a framework and I think that confuses a lot of people, because there is so much noise in the market about zero trust products at the moment. We know from our research that has caused a lot of confusion, and clients have indicated concern about chaos in the market, and it makes it hard for them to figure out where to start.”
A tools-centric focus is neither the way to run the cloud nor achieve a system of zero trust within it. Zero trust involves taking a step back and not just rethinking your security model but changing your view of how the cloud is operated. Delivering zero trust in the cloud, IP-based services and on-demand provisioning, mean viewing the cloud in a way that lets you provision, connect, discover and secure transactions, users, data and applications at scale – regardless of runtime or provider.
This approach requires integrated tools and processes that are managed centrally and automated, rather than a system of manual processes and individual tools or teams arranged around silos.
Fig. 3: Human access and authorization
Identity first, then automation
So how does adopting an operational mindset when it comes to running the cloud deliver an effective system of zero trust?
Zero trust is founded on identity. The root cause of many data breaches is the use of stolen credentials – the second most common cause of threat, according to Verizon’s 2020 Data Breach Report. According to Forrester vice president and principal analyst for security and risk, Chase Cunningham, meanwhile: “Where they [organizations] fell down was with privilege and access control. If your identity or access store is compromised, that is when a breach can go on for days.”
In a system of identity-based access and security, any machine or human must authenticate who or what they are while their identity and policies define what it is they are allowed to do. Delivering that on an operational basis means tools, workflows and processes that are capable of running consistently across runtimes, networks and services as a set of centrally shared services that are automated. What does this look like exactly?
In a model that operationalizes the cloud, zero trust means codifying policies and procedures. Infrastructure is code in the cloud, so it therefore makes sense to administer and operate that infrastructure using policies that have been codified. You need to codify rules for authorization, access, traffic and network configurations across your runtimes and providers.
For this to succeed, however, you need to centralize the management and administration of these policies and procedures. Store, access and distribute the assets that help secure systems, data, applications and users – assets such as tokens, passwords, certificates and encryption keys for all your public, private or hybrid cloud providers. This is important for two reasons.
First, yes, security. Usernames, passwords, API tokens and other assets essential to authorization and authentication and that hackers typically prey upon, are often littered throughout our infrastructures (fig. 3). They have lived in different places – for example, database passwords coded in plain text or configuration files, stored in a Dropbox account or on a wiki. This is a security risk because these assets are easy to obtain. Moreover, they are outside your jurisdiction, so assigning and managing them is beyond your operational control.
Centralization provides a firm basis on which to protect these assets and manage them: acting from a centralized location you can set fine-grained access controls to systems. And, should there be a breach, you are better able to determine who had access and when.
The second benefit of a centralized approach? Managing the lifecycle of credential and security assets. You are in a strong position to create, issue and track security assets such as tokens, usernames and passwords efficiently without the administrative burden that plagues environments where teams manage life cycles using separate tools or manual processes.
The bedrock of this approach is automation, something that makes operations in the cloud manageable and maintainable as rule, but particularly so in a successful model of zero trust security.
It’s automation that means those codified policies on areas such as access and authorization can be applied and enforced in a fast-changing and fluid cloud environment. It also lets you administer and manage security assets such as tokens, usernames and passwords. Automation lets you deliver a zero trust policy that scales. You can codify authorization and traffic rules within encrypted traffic, while also automating identity-based access (fig. 4). Automating policies means they are operated efficiently without need for human interaction. Automation lets you automate network configurations and enable secure connectivity across any cloud or runtime.
Organizations that deploy automated security technologies can save more than $ 1.5 m on the total cost of a breach compared to those who have not automated security, according to IBM.
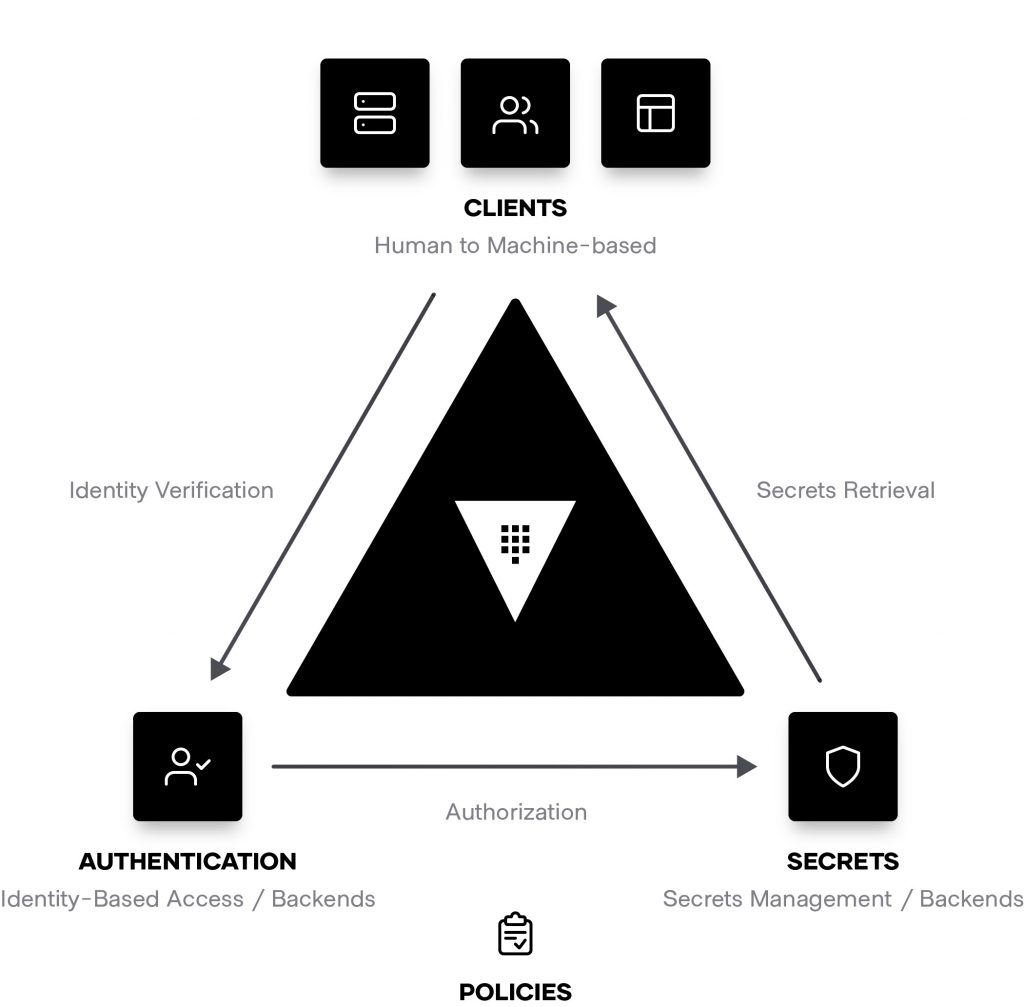
Fig. 4: Machine to Machine Authentication
Conclusion
Zero trust in the cloud is much more than a technology, a set of tools or a security culture. It means reassessing your view of the cloud itself and deciding to run it as a centralized mechanism that you can provision and manage through automation and codified policy. When you operate your cloud in this machine-like way, you have the basis for a model of zero trust that’s scalable and capable of overcoming the complexity that broke the perimeter in the first place.
See also an interview with Chris about the zero trust approach: https://youtu.be/8HhpQqXHumQ
Author:

Chris Kent, Director Product Marketing at HashiCorp
Chris is a tech enthusiast, former entrepreneur with over 20 years experience at startups, Fortune 500 companies, and the US intelligence community.
Sources:
- https://www.darkreading.com/perimeter/never-trust-always-verify-demystifying-zero-trust-to-secure-your-networks/a/d-id/1334995
- https://www.gartner.com/en/newsroom/press-releases/2020-04-03-gartner-cfo-surey-reveals-74-percent-of-organizations-to-shift-some-employees-to-remote-work-permanently2
- https://www.mckinsey.com/business-functions/mckinsey-digital/our-insights/the-covid-19-recovery-will-be-digital-a-plan-for-the-first-90-days
- https://duo.com/resources/ebooks/the-2020-duo-trusted-access-report
- https://thehill.com/policy/cybersecurity/493198-fbi-sees-spike-in-cyber-crime-reports-during-coronavirus-pandemic
- https://www.microsoft.com/security/blog/2020/06/16/exploiting-a-crisis-how-cybercriminals-behaved-during-the-outbreak/
- https://enterprise.verizon.com/en-gb/resources/reports/dbir/
- https://www.ibm.com/security/data-breach
- https://www.pulsesecure.net/resource/2020-EMA-zero-trust-networking-report/
- https://www.infosecurity-magazine.com/news/gartnersec-explicit-zero-trust/
- https://www.ibm.com/downloads/cas/AEJYBPWA
- https://techbeacon.com/security/zero-trust-security-what-it-why-it-matters
- https://techbeacon.com/security/zero-trust-remote-workforces-identity-access-management-key
- https://newsroom.ibm.com/2018-07-10-IBM-Study-Hidden-Costs-of-Data-Breaches-Increase-Expenses-for-Businesses
